Composr Tutorial: Anti-spam settings
Written by Chris Graham (ocProducts)
Attack by spam-bots can be a major problem for a website. Fortunately Composr provides a number of tools to help you.This tutorial will go through the tools available, and our philosophy regarding them.
The actual configuration options are under Admin Zone > Setup > Configuration > Security, and should be reasonably intuitive.
This tutorial does not cover validation, which is covered in the Policing a community site tutorial.
Table of contents
- Composr Tutorial: Anti-spam settings
CAPTCHA
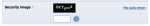
The CAPTCHA
Composr uses a unique method behind-the-scenes to generate the CAPTCHA (the 'CSS' method), which has proven very effective.
Generally-speaking, CAPTCHA will fully protect you from spam. The exception tends to be when real humans do set up accounts, then spam using them. Some spammers subcontract CAPTCHA solution to humans on low-salaries. Other spammers serve target site's CAPTCHAs out to video sites (for example) where viewers unwittingly are made to solve them in order to be allowed to watch a video.
Therefore, we have additional controls.
Alternative CAPTCHA systems, such as solving maths problems, or recognising cats, or answering domain-problems (i.e. something specific about the subject of the website the CAPTCHA is on), are very popular. However this is purely "security through obscurity". A spammer can easily target a specific site's collection of answers, then spam that site enormously – because unlike the regular CAPTCHAs, these CAPTCHAs work on a much more limited set of problems and solutions.
Other CAPTCHA systems use scanned text, or incredibly distorted text, that often even humans don't understand. We don't go with this approach, as it is a terrible user experience.
In other words, Composr's default CAPTCHA tries to be both highly secure, and reasonable for a human to use, and then we have additional protections too.
We have an audio option for the CAPTCHA which is important for users with visual impairments. You can also remove the distortion effects from the CAPTCHA, which makes readability easier, but makes it much easier for a spammer to crack it.
Hidden options (advanced)
These hidden options expand the scope of the CAPTCHA to also cover members:- captcha_member_days – set this to a number if new members should continue to have CAPTCHA for this many days
- captcha_member_posts – set this to a number if new members should continue to have CAPTCHA for this many forum posts
Sample Commandr command:
Code
:set_value('captcha_member_days', '5'); set_value('captcha_member_posts', '5');
Public block lists
Remote Block Lists (RBLs)
Remote Block Lists (RBLs) are a technique whereby Composr checks third-party lists of known spammers, via special RBL-protocols, based on DNS. You don't need to know the technical details other than that Composr can be configured to use an RBL service.We have picked defaults options within Composr to help you get started with the best service(s).
Update: Actually the default list is now empty, as we learnt that there currently aren't any very reliable services for this. Common ones may block too widely, for example blocking computers that were at any point in the last year infected with a virus.
Stop Forum Spam
We use the popular Stop Forum Spam system system to look for known spammers based upon IP address, username, and e-mail address. We also report who you identify as spammers, back to Stop Forum Spam.Options
The options
You can configure when spam checks are performed via the "Spammer checking level" option:
- Every page view (performs RBL checks always, and full check on actions)
- Actions (joining, posting, trackbacks)
- Guest actions (joining, Guest posting, trackbacks)
- Joining
- Never
Some anti-spam services (RBLs, Stop Forum Spam) will provide a 'confidence level' (out of 100) for whether they think an IP address is a spammer. Services that simply return yes/no will be given the value of the 'Implied spammer confidence' option as the confidence level if they say yes.
The confidence level is then compared about a number of configured thresholds:
- Approval (the staff will have to validate a content submission, even if privileges normally say it would go through immediately)
- Block (the attempted action will be blocked)
- Ban (the user's IP address will be banned)
Other options include:
- Specifying how long spam results are cached for
- Specifying how long to trust reports of a spammer that were assigned a "last spam activity" date
Link posting
Absence of the "Post links that search engines will follow" privilege disincentivises users from posting links. Without this privilege all links will have rel="nofollow".Links on member profiles
We entirely block the presence of links on Composr member profiles for members with no posts. The links will automatically reappear once a member has a post, and disappear again if their post(s) are deleted. If the cns_forum addon is not installed then this functionality is not active.This is to disincentivise spammers from flagging your site as an easy way to get links that won't even get moderated away.
Black hole
The black hole in a form's HTML
Project Honey Pot
We integrate the Project Honey Pot service, for injection of a hidden Honey Pot link onto pages. Spambots following the link will flag as spammers in the Project Honey Pot system. This feeds the HTTP:BL block list, which is one of the RBL services Composr can use.You need to specifically configure the options for Honey Pot – it requires you to sign up for their service, and fill in some special configuration options.
Reported posts
If someone spams on the forum (assuming you are running Conversr ) then they can use the 'report post' feature to alert the staff to the spammer activity.This is described in the Policing a community site tutorial.
Guest posting
You may simply want to deny some guest permissions, which will raise the effort spammers have to go to:- Guest posting posting permissions on the forum
- The "Comment upon content" privilege (Admin Zone > Security > Privileges > Feedback)
- The "May report posts" privilege (Admin Zone > Security > Privileges > Members, usergroups and forums privilege)
- Anonymous posts: the "Anonymous posts within private topics" configuration option (Admin Zone > Setup > Configuration > Forum options > Private Topics), and the option individually on forums
This may be enough to deter them.
You may want to also disable permission for Guests to report content.
Per-site Q&A / Probation / Shadow-banning (advanced)
There is a developer addon, antispam_question, which checks the value of a custom profile field to see if it matches a pre-defined setting. If it does not, it puts the member in the Probation usergroup only.You could then then configure your forum permissions so there is only a single forum these members see, that normal members don't. This effectively works as a shadow-ban. You can then move people out of Probation manually if you need to.
The developer addon hard-codes the CPF ID being checked against, and the expected value, and the ID of the usergroup to put failing members in (the default Probation usergroup). It would be fairly easy to customise with minimal coding skills, although ideally we'd add a more extensive configurable feature.
Setting rules
If spam is being posted by real humans, those humans may not realise you have nofollow, and other measures that minimise the effectiveness of their spam.It may be a good idea to explicitly mention your policies on your join page so that human spammers will know they are wasting their time, and thus avoid wasting your time too. The compo.sr site has a good example you can follow.
What we don't do

- Some popular spam checking tools will run checks through a commercial third-party server. We'd rather deliver our code to you within Composr, for improved performance, reliability, and in line with our Open Source philosophy.
- Various alternative CAPTCHA systems (as explained above, under 'CAPTCHA')
Making a spam report to the developers
It is possible that occasionally a spammer may get through Composr's options. If so, please make a thorough report via the https://compo.sr forum – so that we have the chance to properly look into how it got through.Include:
- What exact anti-spam options are configured
- Where the spammer is getting through (e.g. making a forum post)
- The spammer's IP address
- The spammer's user-agent
- The time of the incident
- Whether the spam was by a guest (and if so, if you have guest posting permissions configured)
- An audit trail of pages the spammer went through (to help us identify if it is a bot)
- What is on the spammers member profile (if appropriate)
Avoid being anecdotal or emotional – give clear and concise facts.
Once you've made your report hopefully someone can then tell you what case category you are in:
- Incorrect Composr set up – in which case someone may be able to advise
- Manual spammer attack
- Insufficient protection within Composr – in which case we can consider making Composr improvements
Cleaning up after a forum spammer
The warn/punish form has a spammer mode that allows 1-click disposal of a spammer account, via providing some good default settings on the form. The default settings will delete all their forum posts and topics, and ban/report them in various ways. You can always tune the exact settings each time you action the form but the defaults are usually what you'd want.There are two ways to open the spammer mode:
- The "Deal with as spammer" Audit action from their member profile screen
- By clicking 'Warn' button under a forum post using the middle mouse button (if you have one)
Additional future techniques
Fighting spam is an ongoing challenge. Actual humans are paid to post spam, and increasingly will try and hide spam behind legitimate activity. Ideas for fighting spammer are categorised under the Type: Spam tracker tag.Concepts
- CAPTCHA
- A security image/sound consisting of numbers that a human must enter into a text box. It is designed to prevent bots from spamming your website.
- RBL
- A block list service, detecting whether to block the IP address of a known spammer.
- Spam-bot
- A malicious program a spammer runs, to automatically submit spam to websites. It is often written using techniques similar to that of a search engine crawler (to find targets), and then tries to simulate humans but while posting spam. Some spam-bots run on infected PCs, which is why it can be hard to directly block known spammers.
- Honey Pot
- A hidden link of area where spam-bots may get to, but a human never would. An effective way for detecting spam-bots.
See also
Feedback
Please rate this tutorial:
Have a suggestion? Report an issue on the tracker.